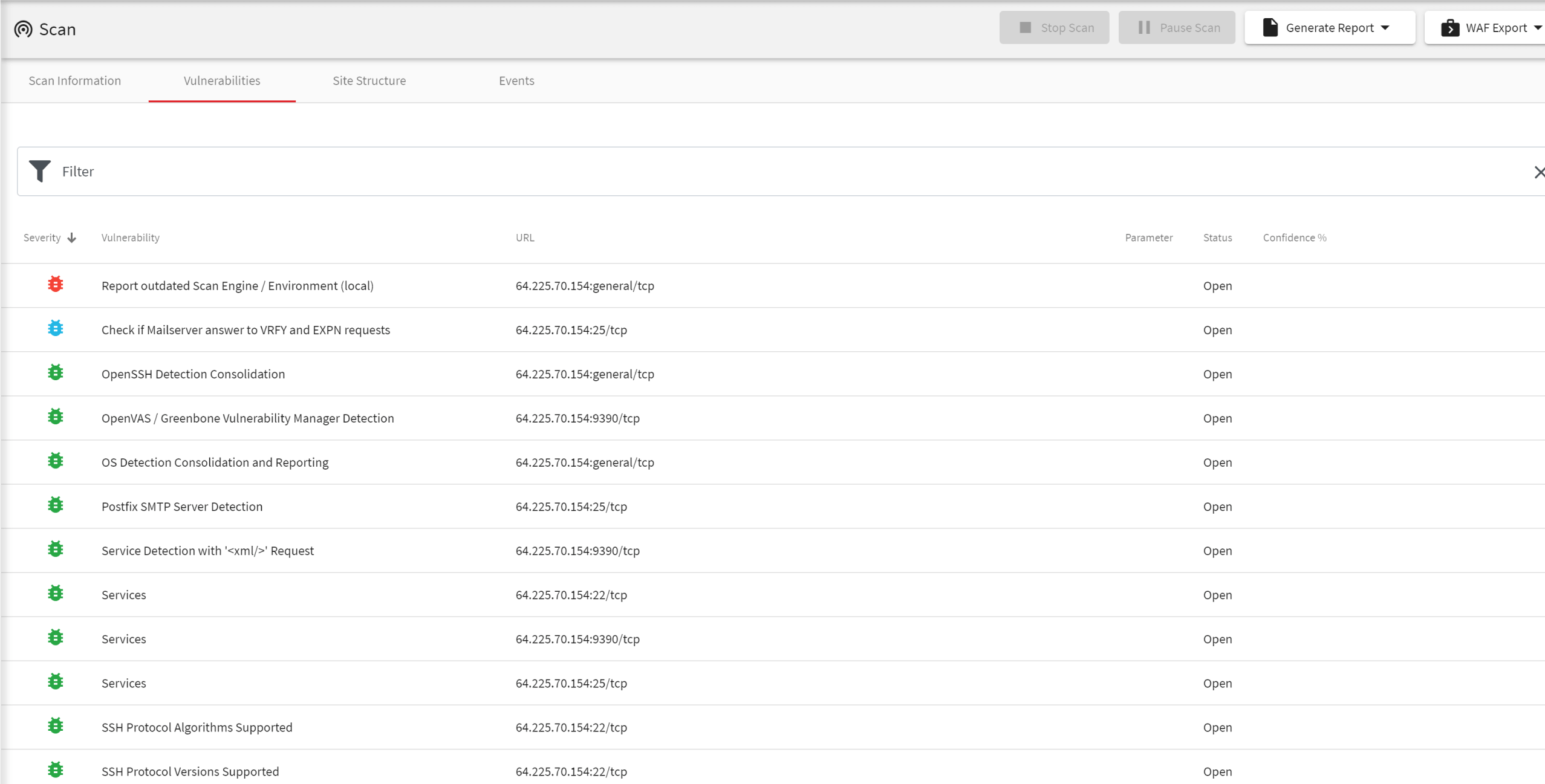
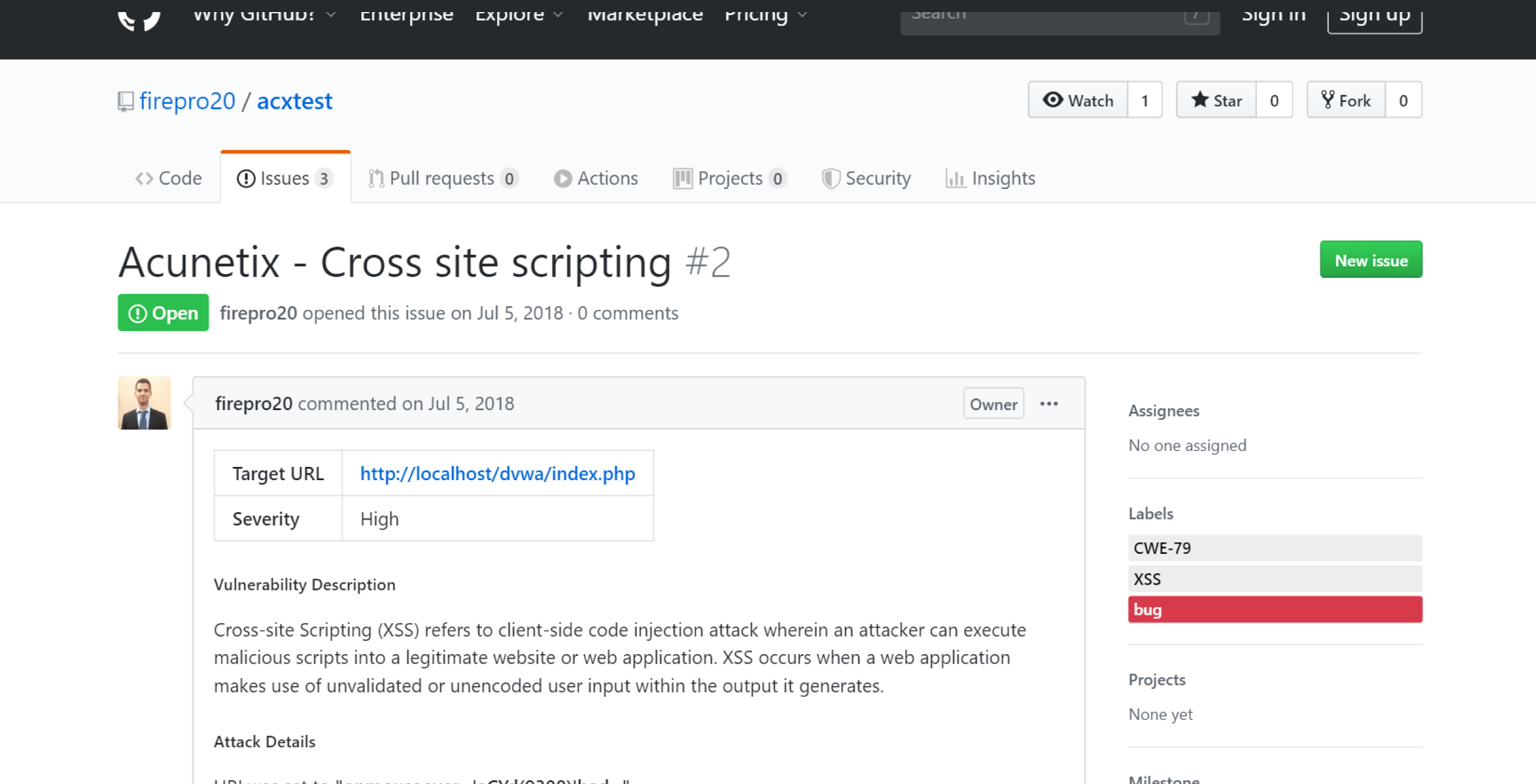
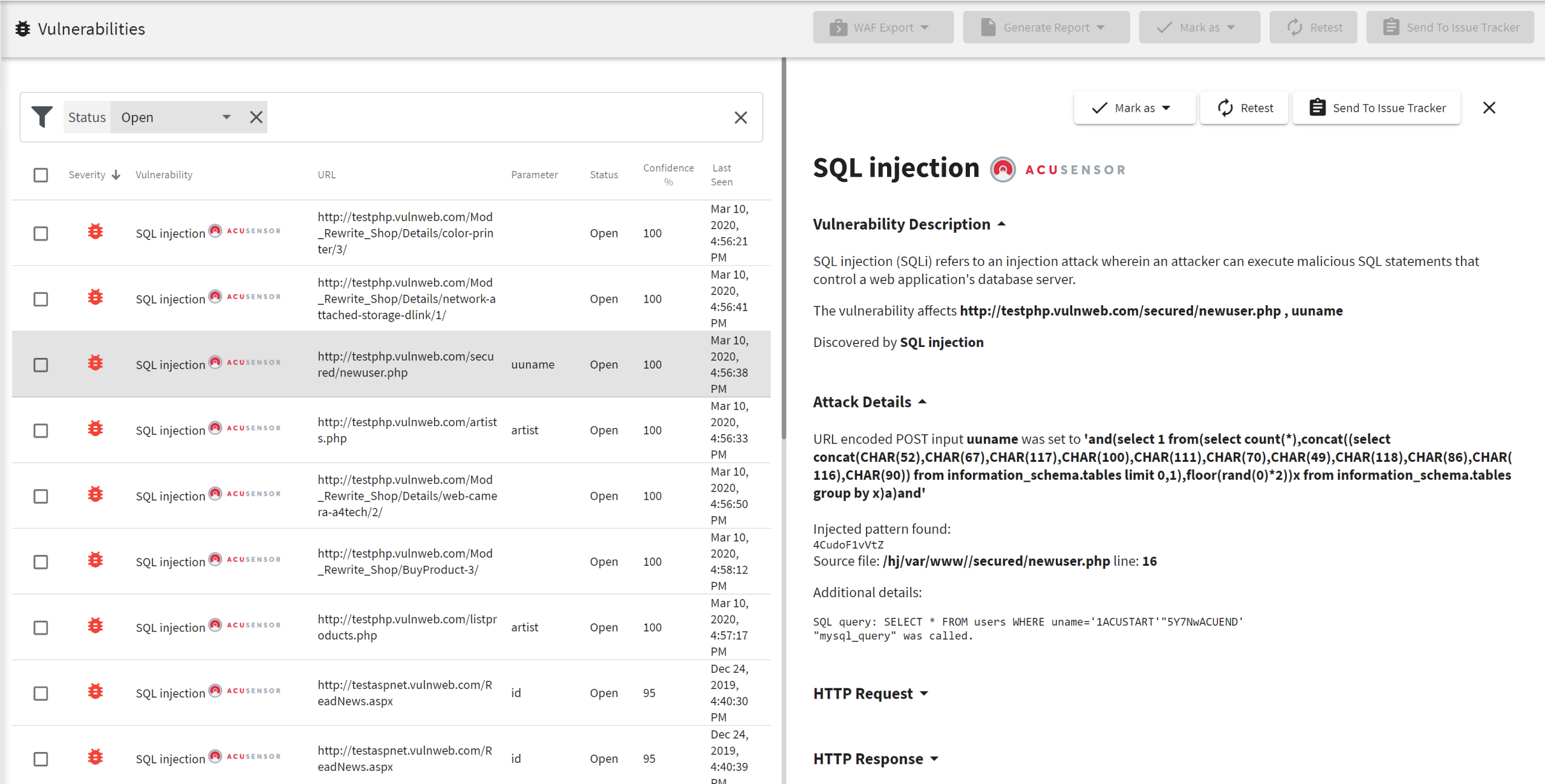
The network scanner requires at minimum MS SQLServer and ISS Site Protector to support it. Ad Eliminate blind spots.

Tool For Ble Security Assessment Ubertooth One Best Offer Electronics And Computers Shop Ineedthebestoffer Com Security Assessment Fun To Be One Assessment
This is where Acunetix fits in.

. Ad Find fix vulnerabilities in your IDE with Snyk Code - efficient actionable code review. A vulnerability scanner is a computer program designed to assess computers networks or applications for known weaknesses. The vulnerability is caused by a tilde character in a GET or OPTIONS request which could allow remote attackers to disclose 83 filenames short names.
Site Home Quick Search. The company offers a 7-day free trial of its profession edition which. Automatically detect vulnerabilities misconfigurations risky software and open ports.
Ad Find fix vulnerabilities in your IDE with Snyk Code - efficient actionable code review. This page lists vulnerability statistics for all versions of ISS Internet Security Scanner. Nessus Essentials formerly Nessus Home from Tenable allows you to scan up to 16 IP addresses at a time.
In the old days of monolithic on-premise applications vulnerability scanners were deployed primarily in the production environment as infrastructure watchdogs that alerted to runtime. Snyks free code checker analyzes your code in real-time and provides fix advice. Vulnerability statistics provide a quick overview for security vulnerabilities of this software.
Nessus is one of the most preferred application vulnerability scanners which remotely discovers potential threats in computers connected to a network. For example some vulnerability scans are able to identify over 50000 unique external andor internal weaknesses ie different ways or methods that hackers can exploit your network. The vulnerability is caused by a tilde character in a GET or OPTIONS request which could allow remote attackers to disclose 83 filenames short names.
Penetration testing goes one step further. Ad Do your applications have the critical Log4j vulnerability. Internet Security Systems Network Scanner 61 is a widely used commercial network-scanning product.
Description Microsoft IIS contains a flaw that may lead to an unauthorized information disclosure. You can view versions of this product or security vulnerabilities. In 2014 Soroush Dalili discovered that newer IIS installations are vulnerable with OPTIONS.
Download our free toolCode Aware for Log4jnow. In fact Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetration testing engagements including malicious attacks. Download our free toolCode Aware for Log4jnow.
Scan systems in local network remote locations and closed network. It involves professional ethical hackers combining the results of automated scans with their expertise to reveal vulnerabilities that may not be identified by scans alone. Ad Do your applications have the critical Log4j vulnerability.
Ad Eliminate blind spots. ISS BlackICE PC Protection 36 cpj and cpu and possibly earlier versions allows local users to bypass the protection scheme by using the ZwDeleteFile API function to delete the critical filelocktxt file which stores information about protected files. Snyks free code checker analyzes your code in real-time and provides fix advice.
Any deeper in the enterprise and it needs to be supplemented by other tools. These scanners are used to discover the weaknesses of a. If all you need is a.
This was publicly disclosed in 2012. The issue is triggered during the parsing of a request that contains a tilde character. Acunetix is a web application security tool that automatically performs a vulnerability assessment of a website or web application and discovers server misconfigurations.
Nessus is an open-source network vulnerability scanner that uses the Common Vulnerabilities and Exposures architecture for easy cross-linking between compliant security tools. Intruder is a cloud-based proactive vulnerability scanner that concentrates on perimeter scanning. If all you need is a vulnerability scanner this is not your best bet.
IIS Short Name Scanner v239 The latest version of scanner for IIS short file name 83 disclosure vulnerability by using the tilde character. Pen testers will also consider your. A vulnerability scan is an automated high-level test that looks for and reports potential known vulnerabilities.
PCI DSS requires two independent methods of PCI scanning. In 2010 Soroush Dalili and Ali Abbasnejad discovered the original bug GET request. Scan systems in local network remote locations and closed network.
Its popularity is proven by the fact that more than 30000 organizations use their services and with 2. Vulnerability scanning is an automated process that identifies your cyber security weaknesses. Vulnerability scanners are the front line of vulnerability managementThey are essential for identifying vulnerabilities that could be used by bad actors to compromise systems and data.
Automatically detect vulnerabilities misconfigurations risky software and open ports. In 2010 Soroush Dalili and Ali Abbasnejad discovered the original bug GET request this was publicly disclosed in 2012. Security Administrator Tool for Analyzing Networks Security Administrator Tool for Analyzing Networks SATAN was a free software vulnerability scanner for analyzing networked computers.
Vulnerability scanning is an automated activity that relies on a database of known vulnerabilities such as CVENVD -- scanning vendors maintain more complete databases -- but does not typically. SATAN captured the attention of a broad technical audience appearing in PC Magazine 1 and drawing threats from the United States Department of Justice. Its known for its timely vulnerability updates and vast reporting capabilities.
The easiest way to get started is to run an automated scan for security holes.

12 Open Source Web Security Scanner Zum Auffinden Von Sicherheitslucken

Katoolin Linux Mint Kali Linux Linux

Vulnerability Scanning Metasploit Unleashed

Performing A Vulnerability Assessment The Ultimate Approach

Pdf Vulnerability Scanners A Proactive Approach To Assess Web Application Security
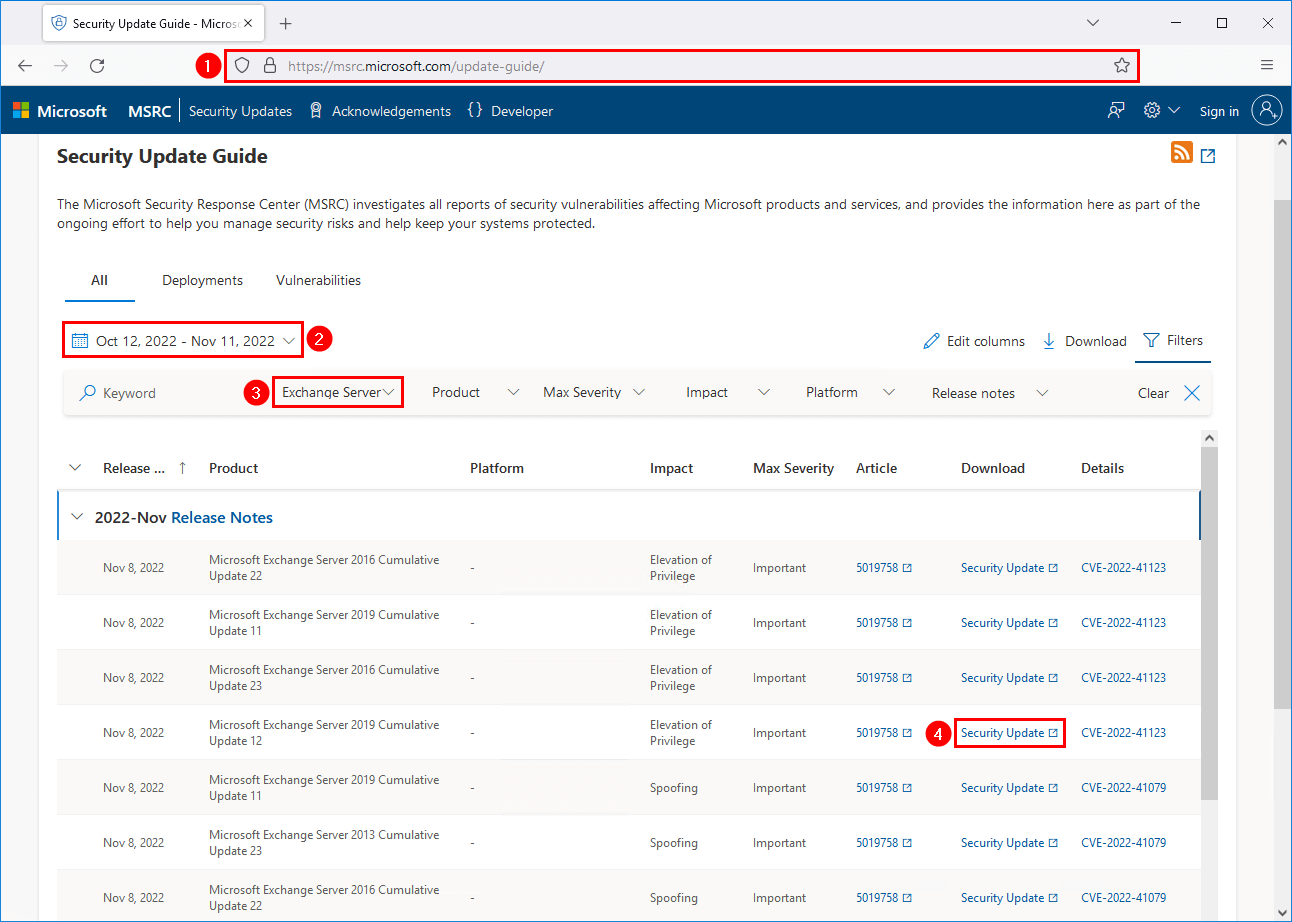
Microsoft Exchange Server Vulnerability Check Ali Tajran
Vulnerability Scanner For Web Servers N Stealth Security Scanner Blog Bujarra Com

Vooki Web Application Vulnerability Scanner Hacking Books Hacking Tools For Android General Knowledge Facts
Vulnerability Scanners Overview Security Weekly Labs

13 Online Free Tools To Scan Website Security Vulnerabilities Malware
Performing A Vulnerability Assessment The Ultimate Approach

13 Online Free Tools To Scan Website Security Vulnerabilities Malware

13 Online Free Tools To Scan Website Security Vulnerabilities Malware